ICENI Device Family
ICENI Overview
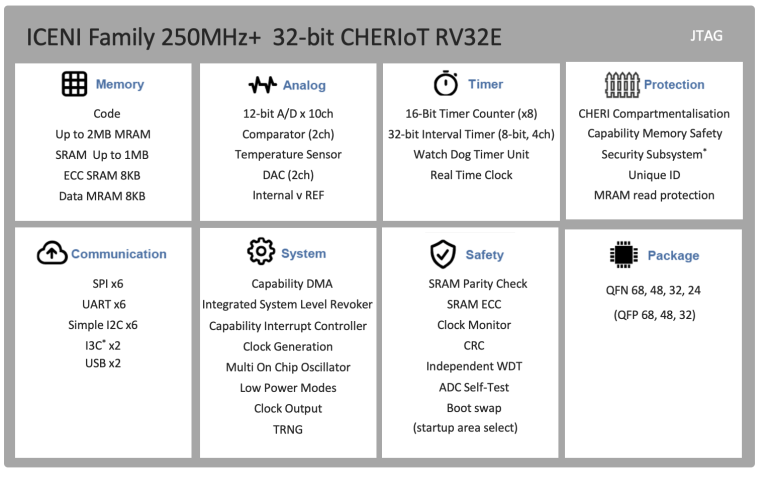
Arriving in 20205 the ICENI family of devices are ideal for a wide array of high-integrity applications, including smart energy, telecoms, medical, automotive and defense applications.
The devices, based on advanced process geometry, deliver outstanding performance in a small form factor, and achieve industry leading compartmentalisation and protection of code.
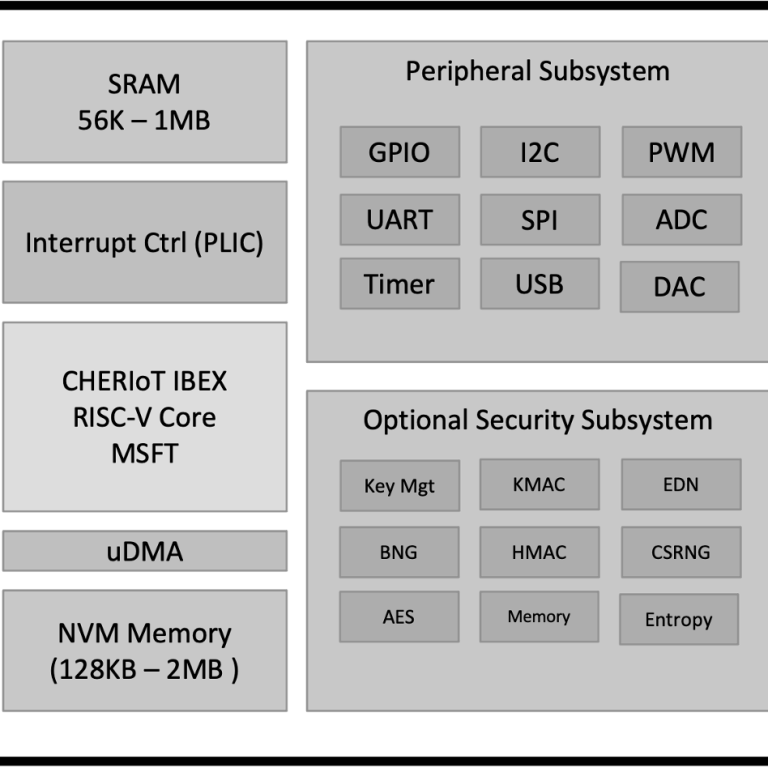
The devices integrate the CHERIoT RV32E core alongside broad system optimisations leveraging CHERI Capabilities. The devices integrate a wide set of standard peripherals depending on the device chosed.
With upto 2MB of non-volatile memory, and 1MB SRAM, these devices bridge the gap between traditional microcontrollers and embedded application processors.
Key Features
- 250MHZ+ CHERIoT-IBEX RV32E Processor
- CHERI Compartmentalisation + Memory Safe architecture
- High Integrity Trusted Code Base (TBC)
Capability Aware Memory & Interconnect
- Up to 2MB single-cycle non-volatile memory
- Up to 1MB SRAM
- microDMA
- PLIC Interrupt Controller
Capability Managed Peripherals
- 32 GPIO
- I2C / SPI / UART
- PWM / Timer
- ADC / DAC*
- USB*
Optional Cryptographic Acceleration Engine (CAE)*
- AES
- Key Mgmt
- KMAC Accelerator
- BNG
- Entropy
All features subject to confirmation.
*Optional features based on device
ICENI
Delivering System & Dynamic Intent
Isolation is easy, you simply disconnect the cables or run multiple processors, however sharing information with isolation is extremely challenging, and sits at the heart of most vulnerabilities. Because system designers don't always know what information will be share, and what must be kept tightly isolated data bleeds across boundaries, creating invisible vulnerabilities that haunt systems throughout their lifetimes.
System Intent
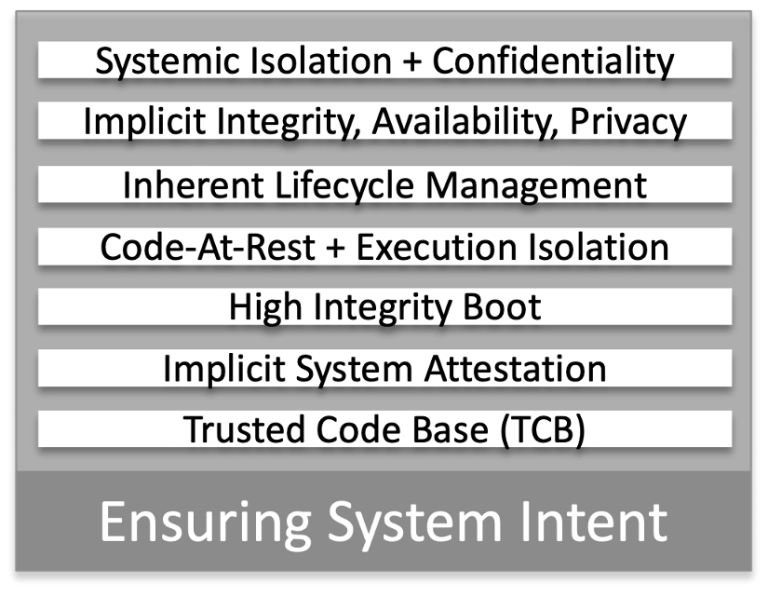
ICENI, and the underlying CHERI technology, is different. Boundaries are set at the correct time, either coming out of boot, or set by the calling function, which enables it to define exactly how the called functions can operate. Formal system delegation becomes a reality and system intent is enforced formally.
With the potential for a tiny Trusted Code Base ( <1KB) it is possible to prove functionality. Once the TCB is defined the expression of compartments via CHERI ensures a high integrity structured boot which passes attestation.
The compartmentalisation model ensure integrity, availabiluty and confidentiality and provides for inherent secure lifecycle management
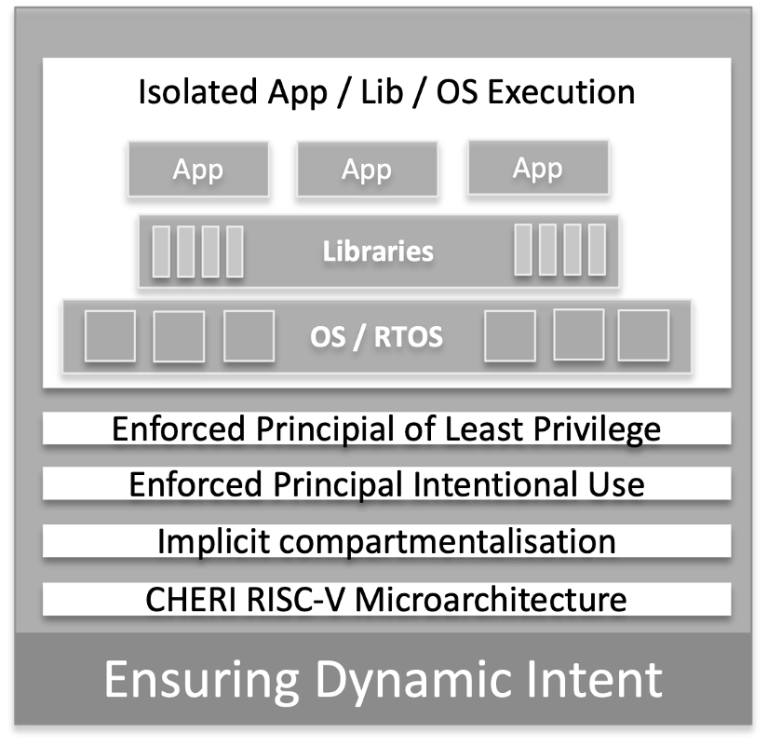
Dynamic Intent
Dynamic intent, or the ability to define and manage exactly how the system operates, in built on the fundamentals of RISC-V and CHERI.
Microsoft built the CHERIoT core on the RV32E architecture, leveraging the open source Ibex core. The advantage of this is that many university and commercial enginering teams have reviewed the RTL code base, and a huge volume of applications have been developed. This means that the core is very well verified and validated, and is already "production ready". The Microsoft team then impelmented the full CHERI architecural extensions on top of the Ibex core, delivering both full compartmentalisation alongside the Memory Safety aspects seen on some other IP implementations. This combination is critical in delivering the two foundational principals of both the Principal of Least Privilege and the Principal of Intentional Use.
The ICENI family are unique in delivering both principals, ensuring full compartmentalisation of RTOS, librarie and applications. Furthermore these principals are available without singificant impact to existing code bases ensuring rapid adoption of the technology and rapid deployment of applications
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
